One Of The Best Tips About How To Prevent Ip Spoofing

You'll have no idea where the problem originates.
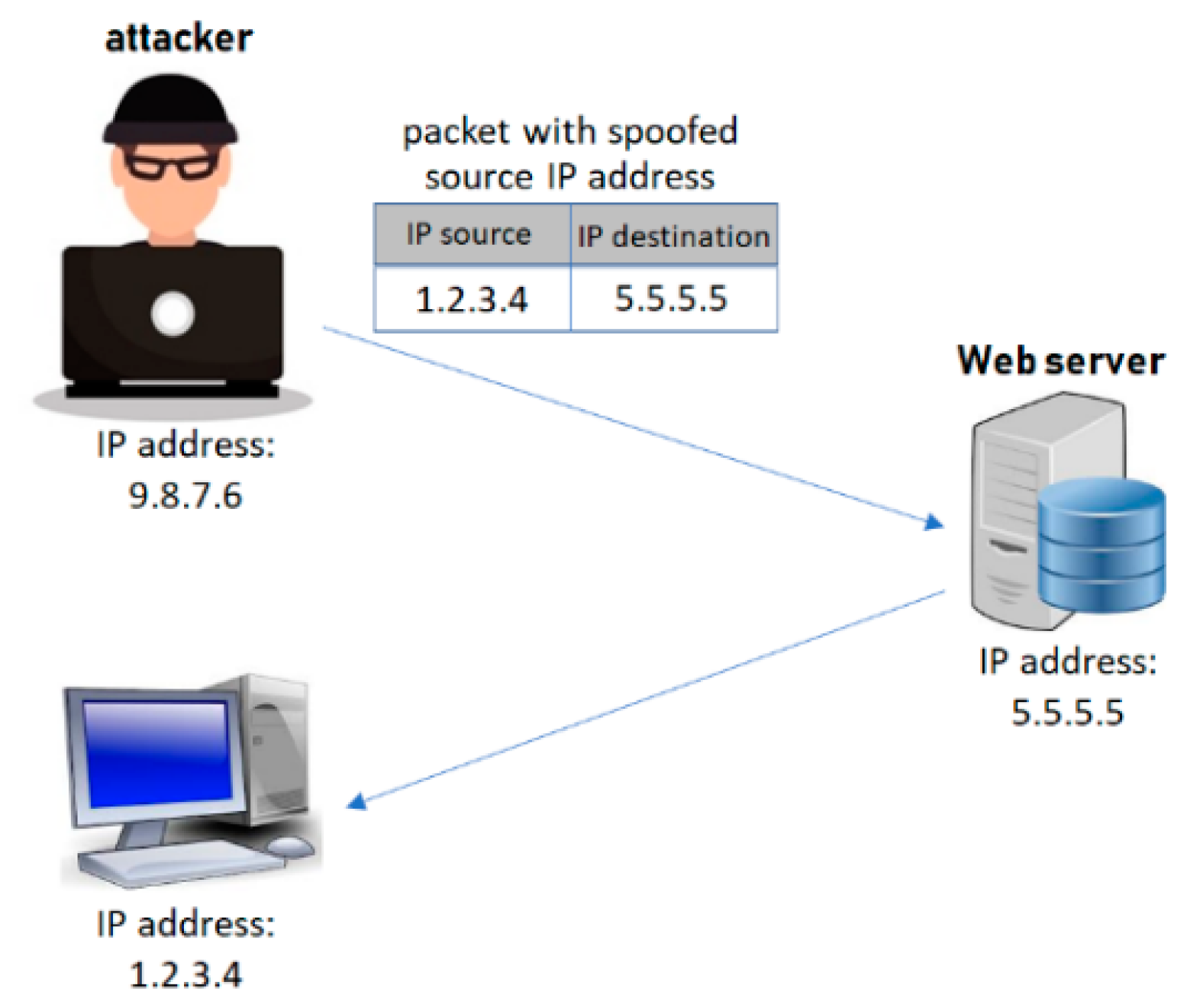
How to prevent ip spoofing. Rpc (remote procedure call services)any service that uses ip address authentication; Since ip address #12 isn't in contoso.com's spf txt record, the message fails the spf check and the receiver may choose. <<strong>ip</strong>_address> and are the ip address and domain of the other email system that sends mail on.</p>
Suppose a phisher finds a way to spoof contoso.com: Deploying packet filtering to detect inconsistencies (such as outgoing. Configuration and services that are vulnerable to ip spoofing:
Monitor networks for unusual activity. Then, monitor your network for suspicious activity with a firewall, which uses a packet filter that inspects ip packet headers. Packet filtering / ingress filtering.
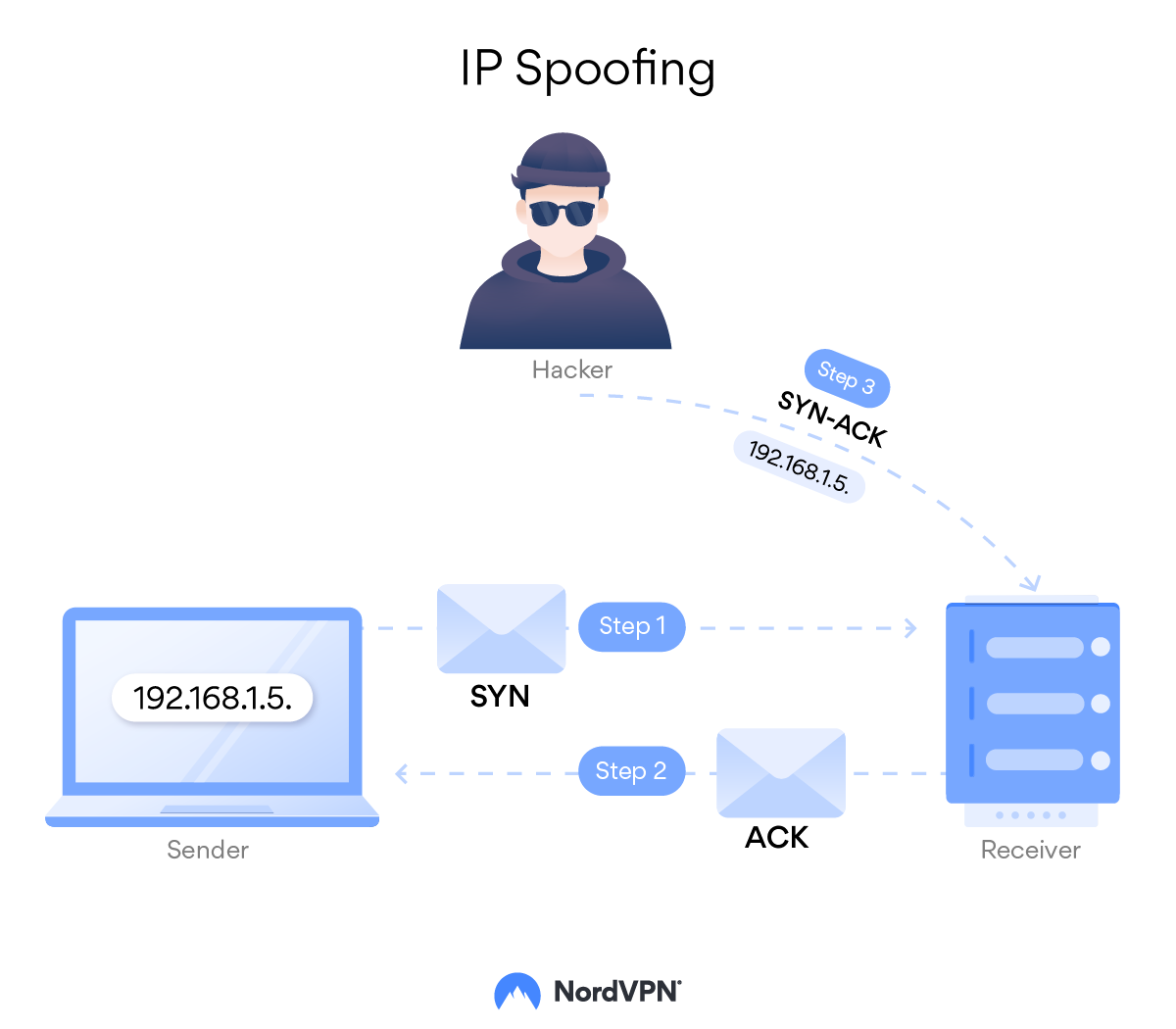
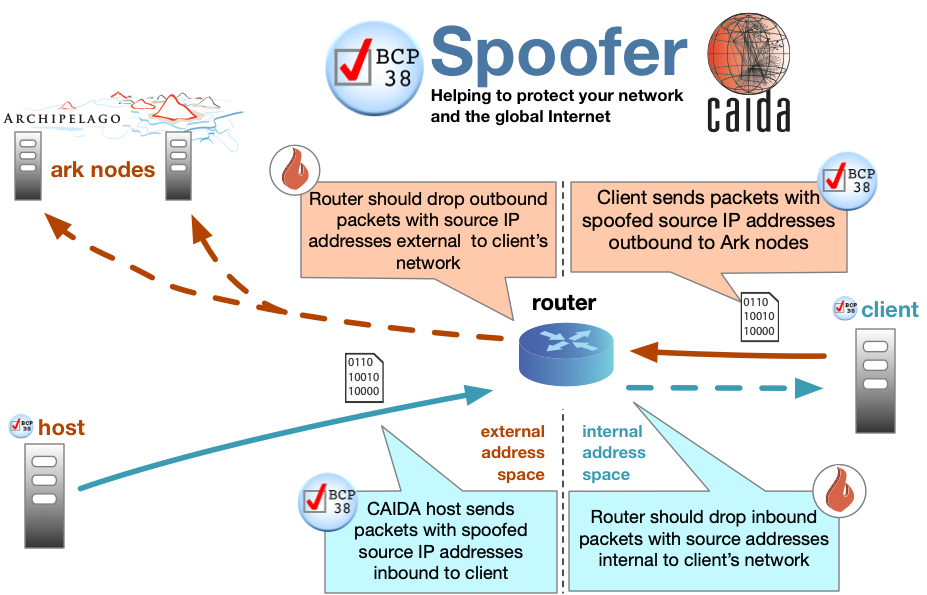
Every device or user attempting to join a network has its ip packets examined. Use strong verification and authentication methods for all remote access. To prevent yourself from ip spoofing negative consequences, you should check the following methods of protection:
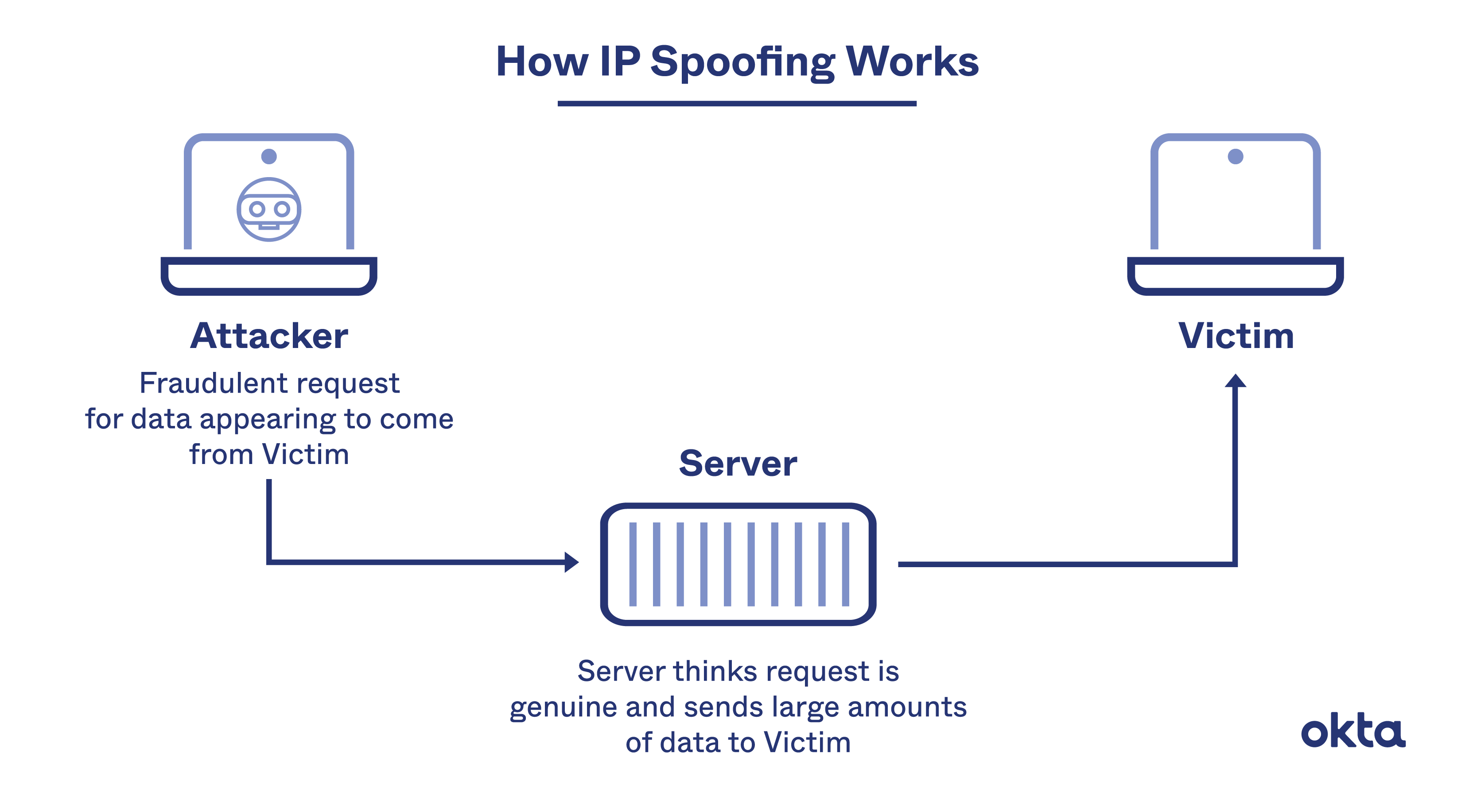
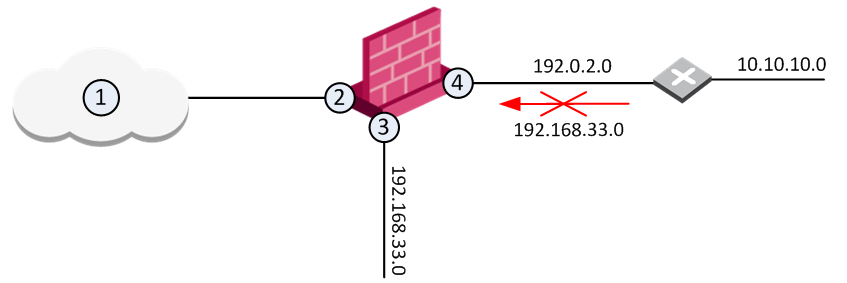
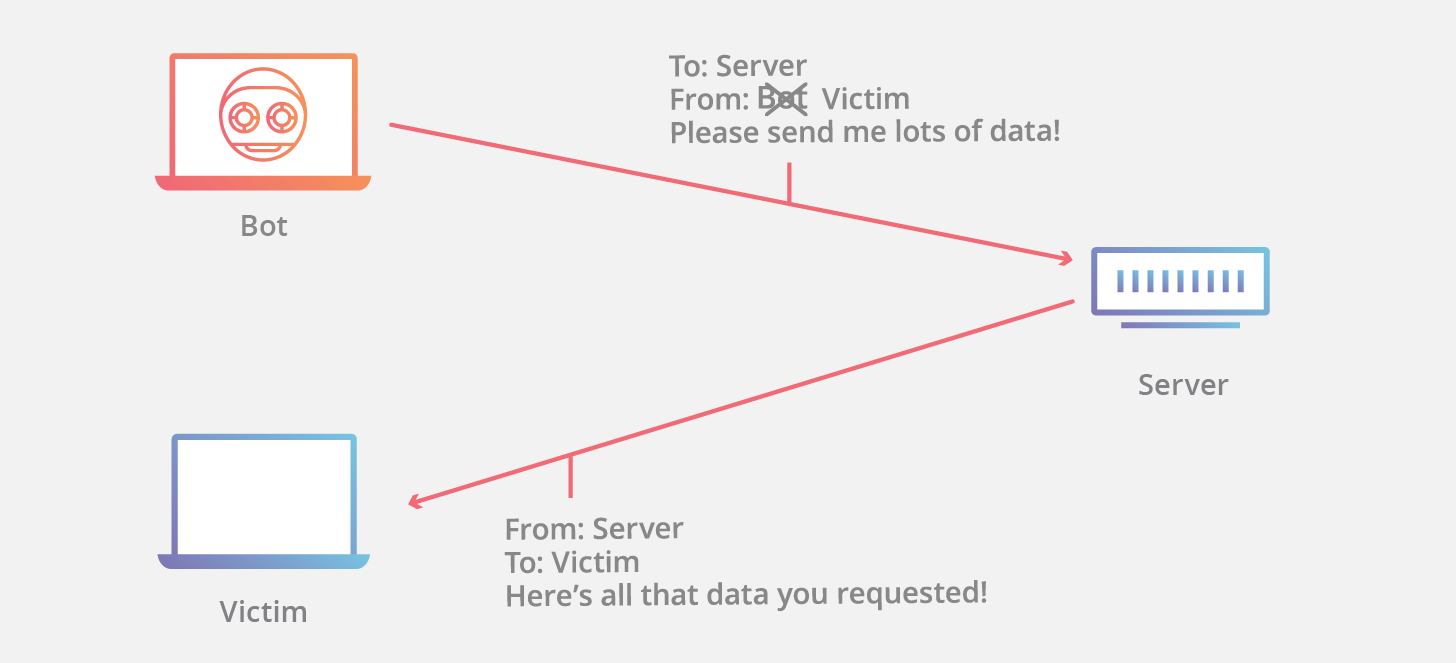
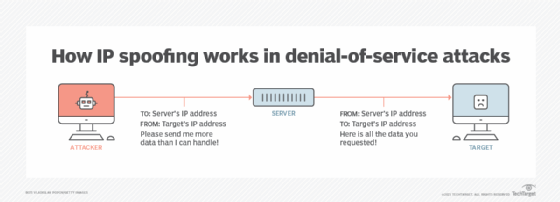
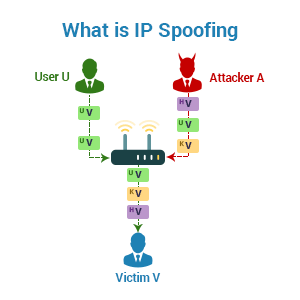
Another effective way to prevent ip spoofing involves configuring routers and switches to deny them entry to packets from outside your local network. Block the ip address that seems to be the source, and you'll block work from a benign computer. Up to 20% cash back whereas email spoofing focuses on the user, ip spoofing is primarily aimed at a network.
Monitoring networks for atypical activity. Do not authenticate devices and users solely. Make an acl of ip.